[Mobile Internet Technology] Medium Access Control
Medium Access Control
Notes from RWTH Aachen University course
“Mobile Internet Technology” Summer semester 2020
professor: Drik Thißen
Medium Access Control
- Controlling when to receive and send data
- idle listening wastes energy
- Multiplexing
- Inflexible
- cannot support bursty traffic
Medium Access Control:
Suitable for wireless data networks
energy-efficent
CSMA/CD
- Ethernet MAC: CSMA/CD
- Carrier sense multiple access / collisions detection
- MAC in wireless
- Contention-based access
- No central coordination
- Carrier sense:
- listen to wire before transmission
- avoid collision with active transmission
- Collision detection:
- listen while transmitting
- In wireless:
- signal strength decreases with distance
- A transmission is not necessarily received by all hosts
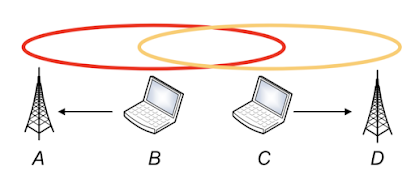
Hidden station
- senders cannot detect each other
- CS fails (C sends to B), then CD fails (A cannot hear the collision)
- collision at receiver
- A is hidden for C
C is hidden for A
Exposed station
- B \(\rightarrow\) A, C\(\xrightarrow[]{\text{wants}}\) D
- CS signals the medium is used (but the other medium isn’t) \(\rightarrow\) C has to wait
- C’s waiting is not necessary
- C is exposed to B
- Medium Access in wireless is difficult because
- Interference situation at receiver
- Impossible to send and receive at the same time
Requirements
- high throughput, low overhead, low error-rate
- energy-efficiency
Energy problems
- Collisions
- Overhearing
- receiving a packet to another node
- Idle listening
- protocol overhead
Centralized Medium Access
- Central station
- Advantages:
- Simple, efficient
- TDMA: voice network
- Polling: small number of devices e.g. Bluetooth
- Disadvantages:
- Burdens the central station
- produces overhead and delays
- Not feasible for non-trivial network sizes
Schedule based MAC
- A schedule exists \(\Rightarrow\) time synchronization needed
- collisions, overhearing, idle listening no issues
Demand Assigned Multiple Access (DAMA)
- Reservation can increase efficiency \(\Rightarrow\) but higher delays
- Example for reservation algorithms:
- Explicit reservation: Reservation Aloha
- Implicit reservation: PRMA
- Reservation-TDMA
Explicit reservation
- Aloha mode: competition, collisions possible
reservation mode: no collisions possible - All stations have to keep a list \(\Rightarrow\) Synchronization
Implicit reservation - Packet Reservation MA (PRMA)
- slots form a frame
- frame repeated
- stations compete for empty slots
- the station can use the following frame
- a slot of frame is empty \(\Rightarrow\) competition
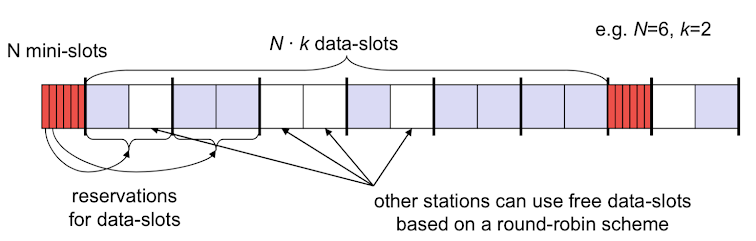
Reservation Time-division MA (TDMA)
- \(N\) mini-slots
\(x\) data-slots - \(x=N\cdot k\)
reserve up to \(k\) data-slots - use mini-slots for reservation
- unused data-slots: Round-robin for other stations
IEEE 802.15.4
- Goal: low-to-medium bit rates, moderate delays without too stringent(嚴格) guarantee requirements, low energy consumption
- Beacon mode:
- Star network: devices are associated with coordinators
- coordinator sends beacon for synchronization/network identification
- active phase (16 slots) + inactive phase (power saving)
- active phase = CAP + CFP (GTS+GTS)
- CAP: contention access period
- CFP: contention free period
- GTS: guarenteed time slots
Contention based MAC
- handle collisions
- Hope: coordination overhead can be saved
- randomization used
- Goal:
How to detect collisions? - How to recover from collisions?
- e.g.
- CSMA/CD
- ALOHA/ Slotted ALOHA
ALOHA
- No central station
- Receiver sends ACK
- Detecting collisions for timing out ACK
- recover: retransmitting
- Pure Aloha:
- no coordination
- no common packet length
- risk of collisions
\(\Rightarrow\) small overlaps destroy both packets
- Slotted Aloha:
- Fixed packet length
- If collision, retransmit with probability \(p\), until successful
Collision avoidance by “Carrier Extension”
- Receiver informs potential interferer
- during an ongoing transmission \(\Rightarrow\) Waste of bandwidth
- before a transmission \(\Rightarrow\) can use the same channel
- busy tone on signaling channel
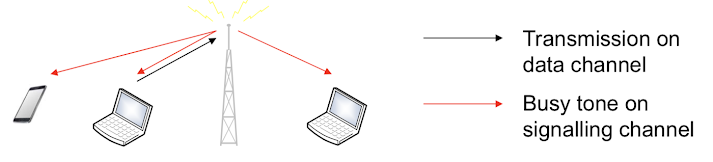
Busy Tone Protocol
- Busy tone multiple access (BTMA)
- Each receiving station sends busy tone
- all stations around the sender will wait
- many exposed station
- Receiver Initiated-BTMA (RI-BTMA)
- only receiver sends busy tone
- few exposed station
- Wireless Collision Detect (WCD)
- BTMA (all stations: "collision detect")
- after decoding receiver address
- then RI-BTMA (receiver: "feedback", others: stop "collision detect")
Multiple Access with Collision Avoidance (MACA)
- Use
- RTS (request to send)
- sender
- CTS (clear to send)
- receiver
- RTS (request to send)
- optional mechanism within CSMA/CA
- Problem: Idle listening
- sleeping will break the protocol (listening RTS/CTS)
- IEEE 802.11 Solution: sleeping and synchronized wake-up
- stations buffer data
- send at pre-arranged points in time









留言
張貼留言