[Mobile Internet Technology] IP and Mobility
IP and Mobility
Notes from RWTH Aachen University course
“Mobile Internet Technology” Summer semester 2020
professor: Drik Thißen
IP and Mobility
- Extend of mobility
- Intra-cell mobility:
- PHY layer
- Inter-cell but Intra-network mobility: (micro mobility)
- local routing / switching
- No change of IP
- Inter-network mobility: (macro mobility)
- change of IP
- handled by special mobility signaling protocols
Mobile IP (MIP)
- TCP/IP: developed for non-mobile, single-homed host
- Dual role of IP address: location, identity

- no secure
\(\Rightarrow\) Mobility: mobile IP
\(\Rightarrow\) Security: IPSec
Mobility
- IP: determines physical subnet
- routing tables not scalable
- IP changes \(\Rightarrow\) breaks transport layer connections
Requirement
- Transparency: mobile device keeps IP
- compatibility: No change in existing routing / devices
- Security: authenticated
- Efficiency and scalability
Concepts: \(\text{basic ID + location ID}\)
components
- Mobile Node(MN)
- Home Agent (HA)
- home network router
- manages MN
- tunnels IP packets to this location (COA)
- Foreign Agent (FA)
- foreign network router
- forwarding tunneled IP packet to MN
- provides COA
- Care-of Address (COA)
- valid address of MN
- managed by FA
- assigned by MN (co-located COA) (via DHCP)
- valid address of MN
- Correspondent Node (CN)
CN\(\rightarrow\) MN

- CN\(\rightarrow\) HA \(\xrightarrow[to\ COA]{\text{encapsulation}}\) FA \(\rightarrow\) MN
MN\(\rightarrow\) CN
- MN \(\rightarrow\) FA \(\rightarrow\) CN
Network Integration
Agent Advertisement: HA, FA periodically announce their existence
Registration: MN \(\xrightarrow[\text{via FA}]{\text{COA}}\) HA
(protected by anthentication)Local Advertisement: HA \(\xrightarrow[\text{as its own addr.}]{\text{IP addr. of MN}}\) access router
- packet to MN: sent to HA
- independent of changes in COA
- HA \(\xrightarrow[]{\text{packet}}\) COA
\(\Rightarrow\) simpler interaction
Encapsulation:
- \((\text{2}^{\text{nd}} \text{ payload}(\text{1}^{\text{st}} \text{ packet}))\)
- IP-in-IP-encapsulation
- tunnel between HA and COA
- minimal encapsulation
- avoid repetition of identical fields
- only for unfragmented packets
- most flexible encapsulation
Optimization of Data Path
- Problem: Triangular Routing
- CN \(\xrightarrow[]{\text{all packets}}\) HA \(\rightarrow\) MN
- especially: MN \(\leftrightarrow\) MN
- Solution: Change of FA
- CN learns (from HA) current location of MN (route optimization)
- (MN registers to new FA new COA)
New FA informs old FA about new COA - old FA: forwards packets, can delete the MN’s registration information
- Problem: Triangular Routing
Further problem
- firewall
- often enforce topologically correct addresses
- multicast
- MN cannot answer
- TTL
- TTL varies from different locations
- security
- CN can learn address ofFA
- CN can track MN
- Solution: Reverse Tunneling

MN\(\rightarrow\) FA \(\require{extpfeil}\Newextarrow{\xRightarrow}{5,5}{0x21D2}\xRightarrow[]{\text{encapsulation}}\) HA \(\rightarrow\) CN- Solves Problems 1.2.3.
- new problems:
- double triangular routing
- Security: FA intrudes home network
- firewall
Mobile IP and IPv6
- IPv6 can simplify mobility support
- Security
- Automatic path optimization:
- IPv6 extension headers
- “Soft” handover
- without packet loss
IPv6 extension header
- Routing
- Destination
Route optimization is mandatory in MIPv6
- CN, MN: binding update
MIP is designed to deal with user mobility
but security, performance
Host Identity Protocol (HIP)
MIP v.s. HIP
- MIP:
- support for un-modified CN
- insfrastructure support (FA,HA)
- indirect mobility management
- Triangular routing
- HIP:
- end-to-en association
- HIP-aware end-host
- direct mobility management
- Authentication, end-to-end security
- no infrastructure support needed
- MIP:
HIP:
- Signaling and key exchange protocol
\(\text{control channel + payload channel}\) - namespace: cryptographic \(\Rightarrow\) mobility, multi-homing
- Signaling and key exchange protocol
Identifier / locator split
- Problem: tight coupling between network / transport layers
\(\Rightarrow\) separation of location (IPv4, IPv6) and identity (HIP)
- applications see stable identity
- routing: locator

- IP can change
- HI (Host Identity) is static
- Network changes hidden from TCP layer
Cryptographic namespace
- Host authentication
- Self-generate private / public key pair
- HI: public key
Globally unique / locally unique Identifiers
- Host Identity Tag (HIT)
- \(\text{HIT = hash (HI)}\)
- IPv6
- Local Scope Identity (LSI)
- \(\text{LSI = Last digits (HIT)}\)
- IPv4
- Restricted to local scope
- Host Identity Tag (HIT)
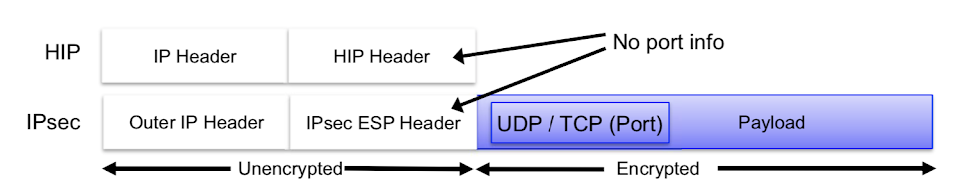
IPSec: Internet Protocol Security
- [IT-security-1] IPSec
Encryption
- Encapsulated Security Payload (ESP)
- Authentication Header (AH)
mode
- Transport mode
- Tunnel mode
replay protection: sequence number
No key exchange protocol
IPSec transport mode with ESP
- end-to-end
- create secure tunnel between two hosts
- ESP header:
- Security Parameter Index (SPI): required for multiplexing
- sequence number
IPSec tunnel mode with ESP
- gateways
- possible to combine with HIP
- Inner header: communicating end-hosts
Outer header: tunnel end-points
IPSec Bound End-to-end Tunnel (BEET) mode with ESP
- IPSec mode + HIP
- Syntactics (表面上): transport mode
Semantics (意義上): tunnel mode - address translation defined by HIP
- Inner IP: HIP host ID
- Outer IP: routable IP address
Mobility \(\leftrightarrow\) Security
- authentication
- re-authentication
- DoS
\(\rightarrow\) careful protocol design
HIP handshake
Information in HIP message
- Host Identity
- Sig
- Diffie-Hellman
- HMAC
- IPSec info
- Puzzle: cryptographic puzzle parameter
Update
- Obtain new IP address
- Transmit new address to peers
- Peer verifies routability
- Peers adjust IPSec tunnel
- Payload uses adjusted tunnel
IPSec rekeying, mobility, multi-homing
Locator: generalization of a network address
Credit-based authentication
- Mobility \(\rightarrow\) redirection-based flooding attacks
\(\Rightarrow\) Credit-based authentication (CBA)
- Idea: limit data rate
- credit = number of bytes received from IP address of the peer
- only send packet if credit suffices
- credit aging decreases
Multi-homing
extension of mobility
host connected through two or more interfaces
multi-homing \(\xrightarrow[]{corresponds}\) mobility signaling
- inform peers locator parameter
- peer runs reachability check
- Multi-homed host can also send locator during BEX
Infrastructure:
- Original: Direct
- middleboxes: indirect
- NAT: compensation for lack of IPv4 addresses
- Firewall: security
- QoS and Proxy: performance
Legacy Middleboxes and HIP
- Strong (theoretical) advantage of HIP architecture
\(\Rightarrow\) But middleboxes can affect HIP packet delivery
- support only limited set of protocols
\(\Rightarrow\) need to create support for legacy middlebox traversal
HIP strategy for legacy middlebox traversal
- UDP encapsulation for HIP and payload
- UDP understood by majority of middleboxes
\(\Rightarrow\) but header overhead, more complex solutions needed
- UDP encapsulation for HIP and payload
PISA
- WiFi drawback
- Threats to mobile node:
- AP MITM attacks, eavesdropping
- Threats to AP:
- illegal mobile node
- Access AP’s LAN
- No roaming between APs
- Threats to mobile node:
- WiFi: trust relations
- Transitive trust relation
- Mobile guest
- Community Operator
- Host AP
Home AP not included
- Transitive trust relation
- PISA: Peer-to-peer-based Wi-Fi Internet Sharing Architecture
- Securely relocate internet access \(\rightarrow\) MN’s home
\[\text{AP provider}\require{extpfeil}\Newextarrow{\xLeftrightarrow} {5,5}{0x21D4}\xLeftrightarrow[]{\text{encrypted tunnel}}\text{mobile guest}\]- security, privacy
- transparent mobility support
- Solve legal liability (法律責任) problem
- Scalable, decentralized solution
- Global mobility and security by
- HIP
- Indirection via “Trusted host”
- Encrypted tunnel
- PISA: trust relations
- \(\text{community}\require{mhchem}\ce{<=>[\text{attest membership (certificate)}][\text{trust}]}\text{Host AP}\)
- \(\text{Host AP}\require{extpfeil}\Newextarrow{\xLeftrightarrow} {5,5}{0x21D4}\xLeftrightarrow[\text{trust}]{\text{transitive}}\text{Home AP}\)
- \(\text{Home AP}\require{extpfeil}\Newextarrow{\xLeftrightarrow} {5,5}{0x21D4}\xLeftrightarrow[\text{trust}]{\text{strong}}\text{Mobile guest}\)
- \(\text{Host AP}\dashrightarrow\text{Mobile guest}\)
No trust necessary between Host AP and Mobile guest \(\Rightarrow\) data encryption - Security concepts in PISA
- Securely relocate internet access \(\rightarrow\) MN’s home
- Authentication of Trust Point
- \(\text{Initiator}\require{extpfeil}\Newextarrow{\xLeftrightarrow} {5,5}{0x21D4}\xLeftrightarrow[\text{Authentication}]{\text{Mutual}}\text{Responder}\)
- PISA extends HIP handshake
- no seperate handshake protocol
- fewer packet, low latency, less complexity
- Mobility with PISA
- PISA extends HIP mobility
- Authentication towards TP
- Host AP can inject nonce and puzzle to enforce Home AP to proof its identification
- PISA extends HIP mobility
- Roaming \(\Rightarrow\) Delay
- AP discovery
- DHCP
- authentication
- mobility signaling
- Parallel scanning \(\Rightarrow\) detecting APs on adjacent channels
- Neighbor detection and coordination
- Handover optimization
- Load balancing
- Channel assignments
- Pre-authentication / Pre-configuration
- Neighbor APs
- Enable TP and AP to assist handovers
- MOBIKE
- Mobility and Multihoming extension for IKEv2
- VPN: remotely connect to home network, protected by IPSec in tunnel mode
- Problem: change of access network \(\Rightarrow\) change of IPSec SAs
- Solution: MOBIKE
- Mobility and Multihoming extension for IKEv2




















留言
張貼留言